
 |
Cisco Config for The Almost Impossible VPN Configuration between 2 Private LANs that Have the Same Subnet Address.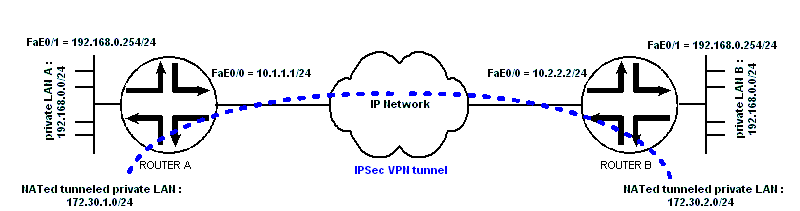 The trick is to NAT traffic between 2 LANs to a different private subnet before tunneling. The VPN traffic will be NATted to another subnet using IOS ip nat pool type match-host feature to a new private subnet address, assigning the same host portion of an IP address and only translate the network prefix portion of the IP address: The hosts on LAN A will see the hosts on LAN B as 172.30.2.0/24, instead of 192.168.0.0/24. The hosts on LAN B will see the hosts on LAN A as 172.30.1.0/24, instead of 192.168.0.0/24. Then configure the crypto access-list on this NATted traffic, the rest is just simple IPSec configuration. The remaining traffic will be NATted using the IP address of router's public the interface for normal Internet navigation. The configuration of ROUTER A: hostname ROUTER_A ! crypto isakmp policy 10 encr 3des hash sha authentication pre-share group 2 crypto isakmp key MYPSK address 10.2.2.2 ! crypto ipsec transform-set TRANS-ESP-3DESSHA esp-3des esp-sha-hmac ! crypto map toremoteLAN_B 10 ipsec-isakmp set peer 10.2.2.2 set transform-set TRANS-ESP-3DESSHA match address 150 ! ! interface FastEthernet0/0 ip address 10.1.1.1 255.255.255.0 ip nat outside crypto map toremoteLAN_B ! interface FastEthernet0/1 ip address 192.168.0.254 255.255.255.0 ip nat inside ! ! ! ip nat pool NEWADDRPOOL 172.30.1.1 172.30.1.254 netmask 255.255.255.0 type match-host ip nat inside source list 110 interface FastEthernet0/0 overload ip nat inside source list 140 pool NEWADDRPOOL ! ip classless ip route 0.0.0.0 0.0.0.0 10.1.1.254 ! access-list 110 remark ACL for Internet access NAT access-list 110 deny ip 192.168.0.0 0.0.0.255 172.30.2.0 0.0.0.255 access-list 110 permit ip 192.168.0.0 0.0.0.255 any ! access-list 140 remark NAT before VPN tunnel access-list 140 permit ip 192.168.0.0 0.0.0.255 172.30.2.0 0.0.0.255 ! access-list 150 remark crypto access-list access-list 150 permit ip 172.30.1.0 0.0.0.255 172.30.2.0 0.0.0.255 The configuration of ROUTER B: hostname ROUTER_B ! crypto isakmp policy 10 encr 3des hash sha authentication pre-share group 2 crypto isakmp key MYPSK address 10.1.1.1 ! crypto ipsec transform-set TRANS-ESP-3DESSHA esp-3des esp-sha-hmac ! crypto map toremoteLAN_A 10 ipsec-isakmp set peer 10.1.1.1 set transform-set TRANS-ESP-3DESSHA match address 150 ! ! interface FastEthernet0/0 ip address 10.2.2.2 255.255.255.0 ip nat outside crypto map toremoteLAN_A ! interface FastEthernet0/1 ip address 192.168.0.254 255.255.255.0 ip nat inside ! ! ! ip nat pool NEWADDRPOOL 172.30.2.1 172.30.2.254 netmask 255.255.255.0 type match-host ip nat inside source list 110 interface FastEthernet0/0 overload ip nat inside source list 140 pool NEWADDRPOOL ! ip classless ip route 0.0.0.0 0.0.0.0 10.2.2.254 ! access-list 110 remark ACL for Internet access NAT access-list 110 deny ip 192.168.0.0 0.0.0.255 172.30.1.0 0.0.0.255 access-list 110 permit ip 192.168.0.0 0.0.0.255 any ! access-list 140 remark NAT before VPN tunnel access-list 140 permit ip 192.168.0.0 0.0.0.255 172.30.1.0 0.0.0.255 ! access-list 150 remark crypto access-list access-list 150 permit ip 172.30.2.0 0.0.0.255 172.30.1.0 0.0.0.255 |
| $ Sun Jan 25 09:31:11 CET 2004 $ | © 2003-2004 Omar Gani |