
 |
Allied Telesyn Config for The Almost Impossible VPN Configuration between 2 Private LANs that Have the Same Subnet Address.1. VPN between 2 remote LANs with same subnet address 2. VPN between 2 remote LANs with same subnet address + enhanced NAT 3. VPN between 2 remote LANs with same subnet address + enhanced NAT + bonus Cisco like loopback config 1. VPN between 2 remote LANs with same subnet address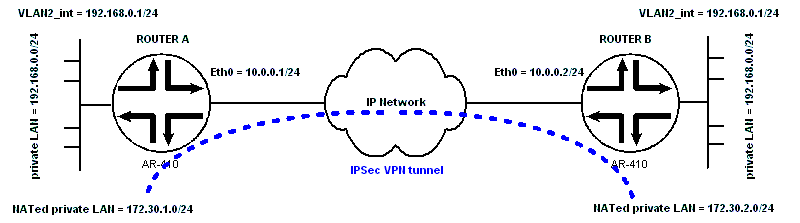 Usually VPN tunnel is configured between 2 remote LANs that have different subnet address... But actually it's also possible to configure VPN between 2 remote LANs that have the same subnet address The trick is to NAT the original LAN private IP addresses to a different private IP addresses, in order to have 2 remote LANs that a have a different subnet address, then configure the VPN using these NATed IP addresses... The config of ROUTER A: # VLAN general configuration create vlan="vlan2" vid=2 # VLAN port configuration add vlan="2" port=1 # IP configuration enable ip add ip int=eth0 ip=10.0.0.2 mask=255.255.255.0 add ip int=vlan2 ip=192.168.0.1 set ip loc ip=192.168.0.1 add ip rou=0.0.0.0 mask=0.0.0.0 int=eth0 next=10.0.0.1 # FIREWALL configuration enable firewall create firewall policy="firepoli" enable firewall policy="firepoli" icmp_f=all add firewall policy="firepoli" int=vlan2 type=private add firewall policy="firepoli" int=eth0 type=public add firewall poli="firepoli" nat=enhanced int=vlan2 gblin=eth0 gblip=10.0.0.2 add firewall poli="firepoli" ru=2 ac=nat int=eth0 prot=ALL ip=192.168.0.0 gblip=172.30.2.0 natm=255.255.255.0 set firewall poli="firepoli" ru=2 rem=172.30.1.0-172.30.1.255 enc=ips add firewall poli="firepoli" ru=3 ac=allo int=eth0 prot=udp po=500 ip=10.0.0.2 gblip=10.0.0.2 gblp=500 add firewall poli="firepoli" ru=1 ac=nat int=vlan2 prot=ALL ip=192.168.0.0 gblip=172.30.2.0 natm=255.255.255.0 set firewall poli="firepoli" ru=1 rem=172.30.1.0-172.30.1.255 # IPSEC configuration create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha create ipsec bund=1 key=isakmp string="1" create ipsec pol="vpn-isakmp" int=eth0 ac=permit set ipsec pol="vpn-isakmp" lp=500 rp=500 tra=UDP create ipsec pol="vpn-tunnel1" int=eth0 ac=ipsec key=isakmp bund=1 peer=10.0.0.1 isa="passphrase" set ipsec pol="vpn-tunnel1" lad=172.30.2.0 lma=255.255.255.0 rad=172.30.1.0 rma=255.255.255.0 set ipsec pol="vpn-tunnel1" srci=eth0 create ipsec pol="vpn-internet" int=eth0 ac=permit enable ipsec # ISAKMP Configurations create isakmp pol="passphrase" pe=10.0.0.1 srci=eth0 enc=3desouter key=1 set isakmp pol="passphrase" gro=2 set isakmp pol="passphrase" sendd=true setc=true enable isakmp The config of ROUTER B: # VLAN general configuration create vlan="vlan2" vid=2 # VLAN port configuration add vlan="2" port=1 # IP configuration enable ip add ip int=eth0 ip=10.0.0.2 mask=255.255.255.0 add ip int=vlan2 ip=192.168.0.1 set ip loc ip=192.168.0.1 add ip rou=0.0.0.0 mask=0.0.0.0 int=eth0 next=10.0.0.1 # FIREWALL configuration enable firewall create firewall policy="firepoli" enable firewall policy="firepoli" icmp_f=all add firewall policy="firepoli" int=vlan2 type=private add firewall policy="firepoli" int=eth0 type=public add firewall poli="firepoli" nat=enhanced int=vlan2 gblin=eth0 gblip=10.0.0.2 add firewall poli="firepoli" ru=2 ac=nat int=eth0 prot=ALL ip=192.168.0.0 gblip=172.30.2.0 natm=255.255.255.0 set firewall poli="firepoli" ru=2 rem=172.30.1.0-172.30.1.255 enc=ips add firewall poli="firepoli" ru=3 ac=allo int=eth0 prot=udp po=500 ip=10.0.0.2 gblip=10.0.0.2 gblp=500 add firewall poli="firepoli" ru=1 ac=nat int=vlan2 prot=ALL ip=192.168.0.0 gblip=172.30.2.0 natm=255.255.255.0 set firewall poli="firepoli" ru=1 rem=172.30.1.0-172.30.1.255 # IPSEC configuration create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha create ipsec bund=1 key=isakmp string="1" create ipsec pol="vpn-isakmp" int=eth0 ac=permit set ipsec pol="vpn-isakmp" lp=500 rp=500 tra=UDP create ipsec pol="vpn-tunnel1" int=eth0 ac=ipsec key=isakmp bund=1 peer=10.0.0.1 isa="passphrase" set ipsec pol="vpn-tunnel1" lad=172.30.2.0 lma=255.255.255.0 rad=172.30.1.0 rma=255.255.255.0 set ipsec pol="vpn-tunnel1" srci=eth0 create ipsec pol="vpn-internet" int=eth0 ac=permit enable ipsec # ISAKMP Configurations create isakmp pol="passphrase" pe=10.0.0.1 srci=eth0 enc=3desouter key=1 set isakmp pol="passphrase" gro=2 set isakmp pol="passphrase" sendd=true setc=true enable isakmp 2. VPN between 2 remote LANs with the same subnet address + enhanced NAT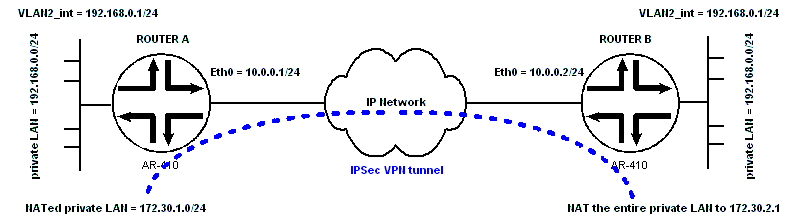 Here is a similar configuration, but this time the all private IP addresses of router B are NATed to a single IP address (172.30.2.1). The config of ROUTER A: same as above The config of ROUTER B: # VLAN general configuration create vlan="vlan2" vid=2 # VLAN port configuration add vlan="2" port=1 # IP configuration enable ip add ip int=eth0 ip=10.0.0.2 mask=255.255.255.0 add ip int=vlan2 ip=192.168.0.1 set ip loc ip=192.168.0.1 add ip rou=0.0.0.0 mask=0.0.0.0 int=eth0 next=10.0.0.1 # FIREWALL configuration enable firewall create firewall policy="firepoli" enable firewall policy="firepoli" icmp_f=all add firewall policy="firepoli" int=vlan2 type=private add firewall policy="firepoli" int=eth0 type=public add firewall poli="firepoli" nat=enhanced int=vlan2 gblin=eth0 gblip=10.0.0.2 add firewall poli="firepoli" ru=2 ac=nat int=eth0 prot=ALL ip=172.30.2.1 add firewall poli="firepoli" ru=3 ac=allo int=eth0 prot=udp po=500 ip=10.0.0.2 gblip=10.0.0.2 gblp=500 add firewall poli="firepoli" ru=1 ac=nat int=vlan2 prot=ALL gblip=172.30.2.1 natt=enh set firewall poli="firepoli" ru=1 rem=172.30.1.0-172.30.1.255 # IPSEC configuration create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha create ipsec bund=1 key=isakmp string="1" create ipsec pol="vpn-isakmp" int=eth0 ac=permit set ipsec pol="vpn-isakmp" lp=500 rp=500 tra=UDP create ipsec pol="vpn-tunnel1" int=eth0 ac=ipsec key=isakmp bund=1 peer=10.0.0.1 isa="passphrase" set ipsec pol="vpn-tunnel1" lad=172.30.2.0 lma=255.255.255.0 rad=172.30.1.0 rma=255.255.255.0 set ipsec pol="vpn-tunnel1" srci=eth0 create ipsec pol="vpn-internet" int=eth0 ac=permit enable ipsec # ISAKMP Configurations create isakmp pol="passphrase" pe=10.0.0.1 srci=eth0 enc=3desouter key=1 set isakmp pol="passphrase" gro=2 set isakmp pol="passphrase" sendd=true setc=true enable isakmp 3. VPN between 2 remote LANs with same subnet address + enhanced NAT + bonus Cisco like loopback config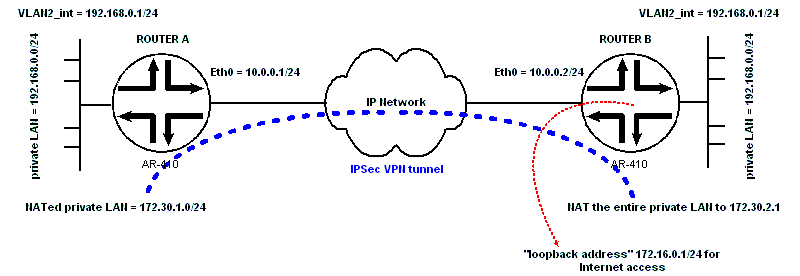 The setup above is similar to the setup no 2. with a little twist: Sometimes ISP assigns a handful of public IP addresses to their client for Internet services and navigation, but the IP address assigned to the client’s router external interface is not a routable IP address. In the setup above the IP address of Ethernet 0 of router B is not routable, the only way to reach router B from the Internet is using 172.16.0.1. Creating a Cisco like loopback interface with the IP address 172.16.0.1 will resolve this problem. All internal will use this IP address for Internet navigation. This IP address is also used as for initiating IPSec VPN and as peer IP address. The config of ROUTER A: # VLAN general configuration create vlan="vlan2" vid=2 # VLAN port configuration add vlan="2" port=1 # IP configuration enable ip add ip int=eth0 ip=10.0.0.1 mask=255.255.255.0 add ip int=vlan2 ip=192.168.0.1 add ip rou=0.0.0.0 mask=0.0.0.0 int=eth0 next=10.0.0.2 # FIREWALL configuration enable firewall create firewall policy="firepoli" enable firewall policy="firepoli" icmp_f=all add firewall policy="firepoli" int=vlan2 type=private add firewall policy="firepoli" int=eth0 type=public add firewall poli="firepoli" nat=enhanced int=vlan2 gblin=eth0 gblip=10.0.0.1 add firewall poli="firepoli" ru=2 ac=nat int=eth0 prot=ALL ip=192.168.0.0 gblip=172.30.1.0 natm=255.255.255.0 set firewall poli="firepoli" ru=2 rem=172.30.2.0-172.30.2.255 enc=ips add firewall poli="firepoli" ru=3 ac=allo int=eth0 prot=udp po=500 ip=10.0.0.1 gblip=10.0.0.1 gblp=500 add firewall poli="firepoli" ru=1 ac=nat int=vlan2 prot=ALL ip=192.168.0.0 gblip=172.30.1.0 natm=255.255.255.0 set firewall poli="firepoli" ru=1 rem=172.30.2.0-172.30.2.255 # IPSEC configuration create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha create ipsec bund=1 key=isakmp string="1" create ipsec pol="vpn-isakmp" int=eth0 ac=permit set ipsec pol="vpn-isakmp" lp=500 rp=500 tra=UDP create ipsec pol="vpn-tunnel1" int=eth0 ac=ipsec key=isakmp bund=1 peer=172.16.0.1 isa="passphrase" set ipsec pol="vpn-tunnel1" lad=172.30.1.0 lma=255.255.255.0 rad=172.30.2.0 rma=255.255.255.0 set ipsec pol="vpn-tunnel1" srci=eth0 create ipsec pol="vpn-internet" int=eth0 ac=permit enable ipsec # ISAKMP Configurations create isakmp pol="passphrase" pe=172.16.0.1 srci=eth0 enc=3desouter key=1 set isakmp pol="passphrase" gro=2 set isakmp pol="passphrase" sendd=true setc=true enable isakmp The config of ROUTER B: # VLAN general configuration create vlan="vlan2" vid=2 # VLAN port configuration add vlan="2" port=1 # PPP configuration create ppp=0 idle=60 over=eth0-any # IP configuration enable ip add ip int=eth0 ip=10.0.0.2 mask=255.255.255.0 add ip int=vlan2 ip=192.168.0.1 add ip int=ppp0 ip=172.16.0.1 mask=255.255.255.255 set ip loc ip=192.168.0.1 add ip rou=0.0.0.0 mask=0.0.0.0 int=eth0 next=10.0.0.1 # FIREWALL configuration enable firewall create firewall policy="firepoli" enable firewall policy="firepoli" icmp_f=all add firewall policy="firepoli" int=vlan2 type=private add firewall policy="firepoli" int=ppp0 type=public add firewall policy="firepoli" int=eth0 type=public add firewall poli="firepoli" nat=enhanced int=vlan2 gblin=eth0 gblip=172.16.0.1 add firewall poli="firepoli" ru=2 ac=nat int=eth0 prot=ALL ip=172.30.2.1 add firewall poli="firepoli" ru=3 ac=allo int=eth0 prot=udp po=500 ip=10.0.0.2 gblip=10.0.0.2 gblp=500 add firewall poli="firepoli" ru=1 ac=nat int=vlan2 prot=ALL gblip=172.30.2.1 natt=enh set firewall poli="firepoli" ru=1 rem=172.30.1.0-172.30.1.255 # IPSEC configuration create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha create ipsec bund=1 key=isakmp string="1" create ipsec pol="vpn-isakmp" int=eth0 ac=permit set ipsec pol="vpn-isakmp" lp=500 rp=500 tra=UDP create ipsec pol="vpn-tunnel1" int=eth0 ac=ipsec key=isakmp bund=1 peer=10.0.0.1 isa="passphrase" set ipsec pol="vpn-tunnel1" lad=172.30.2.0 lma=255.255.255.0 rad=172.30.1.0 rma=255.255.255.0 set ipsec pol="vpn-tunnel1" srci=ppp0 create ipsec pol="vpn-internet" int=eth0 ac=permit enable ipsec # ISAKMP Configurations create isakmp pol="passphrase" pe=10.0.0.1 srci=ppp0 enc=3desouter key=1 set isakmp pol="passphrase" gro=2 set isakmp pol="passphrase" sendd=true setc=true enable isakmp |
| $ Sat Jan 24 20:47:27 CET 2004 $ | © 2003-2004 Omar Gani |